Secure Network Connection at a Remote Site: Best Practices Unveiled
Securing a network connection at a remote site is crucial to protect sensitive data and maintain the integrity of your network. In this post, we will explore several best practices to help you establish a secure network connection at a remote site.
What protocol to set up a secure network connection at a remote site?
Greetings! I am currently responsible for configuring a secure network connection at a remote site on behalf of my organization. Our primary objective is to safeguard data confidentiality, integrity, and user authentication. In light of these crucial requisites, I would be delighted to provide you with recommendations regarding the protocol(s) most suitable for establishing a secure network connection at a remote site. I sincerely value any insights, experiences, or suggestions you may have on this matter. Your support is genuinely appreciated!”
- Question from a user
Best practices to ensure a robust and secure network connection at remote sites
In today's interconnected world, remote sites play a crucial role in many organizations' operations. Whether it's a branch office, a satellite location, or a telecommuting setup, maintaining a secure remote network access is paramount. This article will explore key considerations and best practices to ensure a robust and secure network connection at remote sites.
Implementing Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are fundamental to secure remote connectivity. By encrypting data traffic between the remote site and the central network, VPNs provide a secure tunnel that shields sensitive information from unauthorized access. Organizations should deploy VPN solutions that employ robust encryption protocols, such as OpenVPN or IPsec, and regularly update them to address potential vulnerabilities.
Secure Shell (SSH)
SSH provides secure remote login capabilities and allows for encrypted data transfer. It uses strong encryption algorithms to protect the confidentiality and integrity of data exchanged between the client and the remote server. SSH can be used for secure file transfers, remote command execution, and tunneling other protocols.
Firewall protection
A reliable firewall is essential for securing network connections at remote sites. It acts as a barrier, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. Organizations should deploy firewalls that offer comprehensive features like intrusion detection and prevention, deep packet inspection, and application-level filtering. Regular updates and patches must be applied to ensure the firewall's effectiveness against emerging threats.
Two-Factor Authentication (2FA)
Do you know how to perform secure remote access? Enforcing two-factor authentication adds an additional layer of security to remote network connections. By requiring users to provide two pieces of identification (typically a password and a unique code generated by a mobile app or hardware token), the risk of unauthorized access is significantly reduced. Organizations should implement 2FA solutions to secure access to remote network resources, minimizing the chances of successful brute force attacks or stolen credentials.
Network segmentation
Implementing network segmentation helps minimize the impact of potential breaches by isolating different sections of the network. By dividing the network into segments and applying access controls, organizations can restrict unauthorized lateral movement within the network. This approach enhances security by limiting the potential attack surface and containing any security incidents that might occur.
Regular security audits and updates
Maintaining a secure network connection at remote sites requires ongoing vigilance. Regular security audits help identify vulnerabilities and areas that require improvement. Organizations should conduct penetration testing, vulnerability assessments, and security audits to assess the effectiveness of security measures. Additionally, keeping all network devices, including routers, switches, and firewalls, up to date with the latest firmware patches and security updates is critical to address known vulnerabilities.
Employee education and awareness
Even the most robust security measures can be compromised if employees are unaware of potential risks and best practices. Organizations must invest in comprehensive security awareness training programs for employees at remote sites. These programs should cover topics such as identifying phishing attempts, secure password practices, and the importance of regularly updating software. By fostering a culture of security awareness, organizations can mitigate the human element in security breaches.
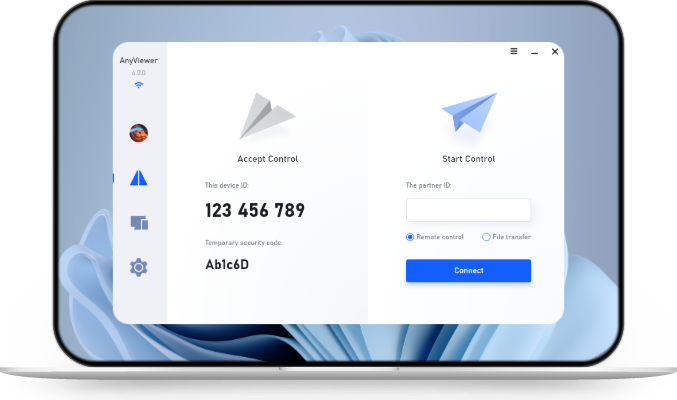
AnyViewer: Unlocking secure and efficient remote access
AnyViewer is an advanced remote desktop software that provides secure network connections while offering exceptional performance and ease of use. Here are the key benefits of using AnyViewer:
►Advanced encryption and security. AnyViewer employs robust encryption protocols, including end-to-end encryption, to protect data during remote sessions. This ensures that sensitive information remains confidential and guarded against unauthorized access, giving you peace of mind while accessing remote sites.
►Lightning-fast performance. With AnyViewer, you can experience lightning-fast performance and real-time responsiveness during remote desktop sessions. Its optimized compression algorithms and streaming technology minimize latency, even over low-bandwidth connections, providing a smooth and efficient user experience.
►User-Friendly Interface. AnyViewer prides itself on its intuitive and user-friendly interface. Navigating through the software is straightforward, making it accessible to both novice and experienced users. The simplicity of AnyViewer's design ensures a hassle-free remote desktop experience without compromising on security or performance.
►Advanced features. AnyViewer offers an array of advanced features designed to enhance work collaboration and productivity, key features including one-click remote control, flexible file transfer, multiple sessions, multi-monitor navigation, real-time chat. These are just a few of the many powerful features that AnyViewer brings to the table, making it an excellent choice for seamless and efficient remote access.
Using AnyViewer is a breeze. Simply download and install the software on your computers to get started!
Step 1. Launch AnyViewer on your host computer. Next, proceed to create a new account by providing your email address and selecting a password, then log in.
Step 2. On the client computer, launch AnyViewer and log in using the same account credentials that you just created. As you successfully log in, the client computer will automatically assign itself with your account.
Step 3. Navigate to the Device section. Here, you will find a list of available devices. Select the specific device you wish to connect to. To initiate the connection, simply click on the One-click control option.
- Notes:✎...AnyViewer offers flexible and cost-effective licensing options to cater to commercial needs. If you require a reliable remote support solution for your business, AnyViewer has you covered with its affordable pricing tiers and benefits:
- One-click up to 100 devices with ease.
- Boost your productivity with the ability to connect to up to 10 devices simultaneously.
- Perform unlimited simultaneous transfers of large files up to a remarkable 1TB in size per file.
- Connect in privacy mode that safeguards your sensitive information by blackening the screen and disabling the keyboard and mouse of the host PC.
- ...
Conclusion
Ensuring the establishment of a secure network connection at a remote site is of utmost importance when it comes to safeguarding your organization's valuable data and maintaining the integrity of your network. This article presents a set of best practices that, when implemented, can bolster your network's security and effectively reduce potential risks. It is crucial to adopt a proactive stance and remain constantly vigilant in order to protect your remote access. Experience the advantages offered by AnyViewer, a tool that not only enhances your productivity but also upholds the most stringent security standards.