This article mainly describes how the Enterprise version allows different permissions to be configured for sub accounts, including user management, device management, and controllable devices.
The role-based permissions feature of AnyViewer Enterprise Edition is crucial for precise management, rational allocation of permissions, and information security within an organization. Administrators can use the role and permissions functionality to create sub-account role groups for employees at various levels and set corresponding permissions for each group.
This feature can be effectively utilized in the following scenarios: by assigning specific role-based permissions, you can restrict sub-accounts under different roles to access and operate only certain functions, preventing unauthorized access and potential data breaches.
For example, sub-accounts in the finance department can only remotely access computers in the finance department, while sub-accounts for technical support can only access computers in the technical support department. For temporary projects or short-term tasks, temporary roles can be created and assigned corresponding permissions. Once the task is completed, these permissions should be promptly revoked to avoid long-term security risks.
The Any viewer Enterprise Edition management center provides a detailed list of two major modules: Device Management and User Management. Let's learn more about it.
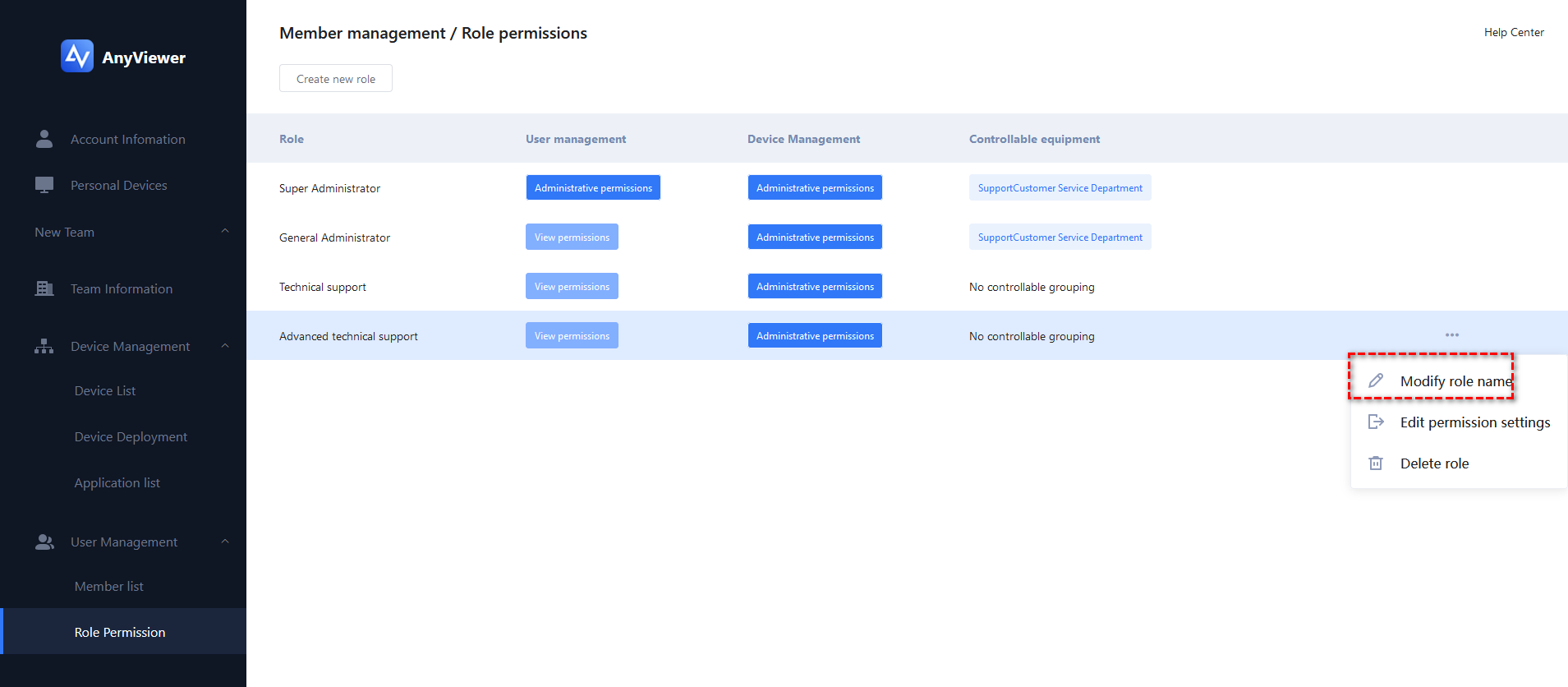
When you add a sub-account successfully, the account will be listed in the Use Management-Member list, where you can change the role.

If you want to add new role. You can click Use Management-Role Permission to create a new role.

In this Role permission page, you can also edit the role name, permission settings and delete the role in this step.
Enterprise Edition now allows you to configure different permission for sub-account user, including user management, device management and controllable devices.
User Management permission
three types of permissions can be set: no permission, view permission, and administrator permission. You can set whether sub-account user under a role have right to access to the User Management page, add sub-account, modify member notes, removing members, creating new roles, or edit role permission.
No permission: if you check this options, the Management Center interface will hide Member List page and Role Permission Page.
View permission: you can view Member List page and Role Permission Page.
Administrator permission: sub-account user under this role have permission to add sub-account, modify member notes, removing members, creating new roles, and edit role permission
Device Management
it also includes such three options. You can set whether the sub-account user under a role have right to access the Device Management page, or move/delete the deices and so on.
No permission: if you check this options, the Management Center interface will hide Device List page and Application list Page, only list the deployment device list page.
View permission: sub-accounts under this role can view Device List page and the Deployment device list page, and they can deploy device and download the MSI package. But the application list page can be hidden.
Administrator permission: sub-accounts under this role can create/delete/rename groups, or delete controllable devices/move controllable devices groups, and approve application lists.
Controllable equipment
Sub-account users need to add devices to the corresponding role, then Sub-accounts under the corresponding roles can remotely control these devices or manage the devices of each department accordingly. If devices are not added to the corresponding role, when you log in to a sub-account under that role in the AnyViewer program, the devices that have not been added will not appear in the "My Devices" list.
In conclusion, Enterprise Edition is committed to providing enterprise organizations with more efficient and secure remote desktop solutions, through various measures to enable business managers to rapidly deploy and efficiently manage remote devices within the enterprise. To provide strong support for enterprise information security, and help further improve the enterprise data security architecture.